Kerberos

Kerberos, though a complex topic, can be better understood by drawing parallels with a hotel analogy. Imagine the Kerberos system as a hotel, and its various components as essential services within this hotel.
At its core, Kerberos is a network authentication protocol akin to the hotel’s front desk, responsible for securely authenticating guests (clients) and services (servers) over an otherwise unsecured network. Just as guests must check in at the front desk to access the hotel’s facilities, users and services in a computer network undergo an authentication process with Kerberos to gain access to resources.
The primary aim of Kerberos is to ensure the security of this authentication process and the data exchanged between clients and servers, symbolized by the hotel’s focus on safeguarding guest identities and their valuable belongings.
In summary, Kerberos, like a well-managed hotel, guarantees a safe and controlled environment for users and services, protecting sensitive information while facilitating secure communication over a potentially vulnerable network. By using this hotel analogy, the intricate workings of Kerberos become more accessible to grasp and comprehend.
Components
Before delving into the Kerberos process, let’s first understand the various components involved.
In Kerberos, the concept of a Realm can be likened to the “Hotel Premises” – a logical boundary encompassing all hotel facilities and services. To access any hotel service, guests are required to undergo authentication within this realm.
The key components of Kerberos include (with the hotel analogy in brackets):
Principal (Guest): In our hotel analogy, a guest represents a user or a service that wants to access various hotel facilities or services. Each guest has a unique identifier, like a room number or a name, that distinguishes them from others in the hotel.
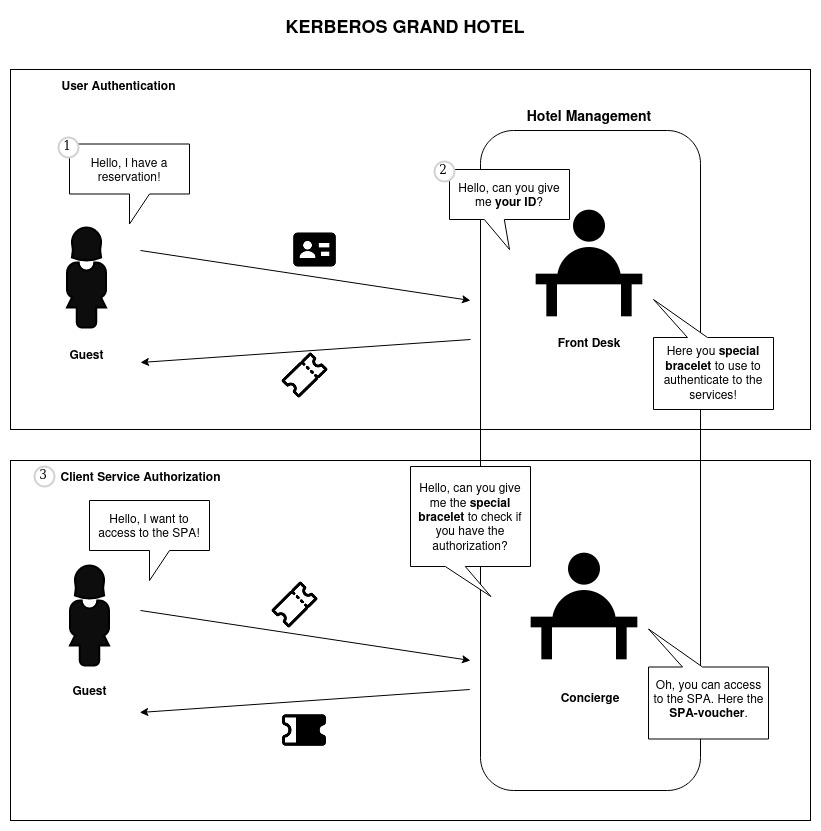
Authentication Server - AS (Front Desk): The hotel’s front desk is like the Authentication Server in Kerberos. When a guest arrives at the hotel (wants to access services), they must first check in at the front desk. Here, the front desk authenticates the guest’s identity by asking for identification (e.g., a passport or driver’s license). Once verified, the front desk issues a special bracelet (TGT) that allows the guest to access various hotel services during their stay.
Ticket Granting Server - TGS (Concierge): The hotel’s concierge represents the Ticket Granting Server. After the guest checks in and receives the special bracelet (TGT) from the front desk, they can approach the concierge whenever they want to use specific hotel services (e.g., spa, restaurant, gym). The concierge will issue a service-specific voucher (service ticket) that grants the guest access to the requested service.
Key Distribution Center - KDC (Hotel Management): The hotel management plays the role of the Key Distribution Center. It oversees the front desk (AS) and the concierge (TGS). The management ensures that both the front desk and concierge have access to the necessary information to authenticate guests and issue service-specific vouchers. It also handles the generation and distribution of encryption keys (room keys) used for securing access to the services.
Ticket (Special Bracelet): The special bracelet given by the front desk (AS) is like the Ticket in Kerberos. It serves as proof of identity and allows the guest (principal) to request access to various services without re-authenticating repeatedly.
Service Ticket (Service-Specific Voucher): The service-specific voucher issued by the concierge (TGS) is similar to the Service Ticket in Kerberos. It is used by the guest to access specific hotel services (e.g., spa, restaurant) without revealing their original identification repeatedly.
For completeness, two other components are present in Kerberos:
The Session Key (Room Key): The room key represents the Session Key in Kerberos. It is a temporary key provided to the guest for securing communication with a specific service (e.g., hotel room). The guest and the service (e.g., hotel room lock) use this key to encrypt and decrypt their communication during the stay.
The Clock Skew (Clock Synchronization): To ensure smooth operations, the hotel management (KDC) ensures that all clocks in the hotel (AS, TGS, and services) are synchronized. This avoids confusion and prevents problems that could arise due to time differences.
Kerberos Process
In our hotel analogy, Kerberos allows guests (users/services) to check in (authenticate) at the front desk (AS) to obtain a special bracelet (TGT). With this bracelet, they can approach the concierge (TGS) to get service-specific vouchers (service tickets) that grant them access to various hotel services without revealing their identity repeatedly. The hotel management (KDC) ensures that the front desk and concierge have the necessary information and keys to facilitate this process within the hotel premises (realm).
Now that we have an understanding of the Kerberos components, let’s explore the authentication process.
Guest Arrival (User Authentication Request: Imagine a guest (user) arriving at the hotel (Kerberos system) and wanting to access various services (resources) like the spa, restaurant, and gym.
Checking In at the Front Desk (Authentication Server - AS): The guest (user) approaches the front desk (AS) and presents their identification (username and password). The front desk (AS) verifies the guest’s identity (authentication) by checking the provided credentials against its database. If the credentials are valid, the front desk (AS) issues a special bracelet (TGT - Ticket Granting Ticket) to the guest (user).
- Getting Service Vouchers (Service Tickets): Now, with the special bracelet (TGT), the guest (user) can access different services (resources) in the hotel (Kerberos realm) without re-authenticating each time. Suppose the guest wants to use the spa (service) first. They go to the concierge (TGS) and present their bracelet (TGT) along with a request for the spa service. The concierge (TGS) checks the bracelet (TGT) to verify the guest’s identity (authentication). Once verified, the concierge (TGS) issues a service-specific voucher (service ticket) for the spa.

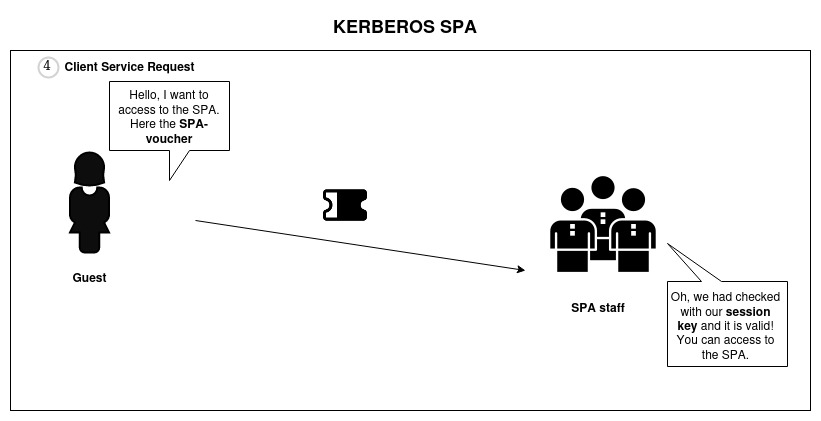
I know, I know! There is no bracelet in the image but I'm not able to draw it! I'm sorry 😔 - Accessing the Service (Resource): With the spa service ticket in hand, the guest (user) goes to the spa entrance (service) and presents the service ticket to the spa staff (resource). The spa staff (resource) checks the service ticket and validates it by decrypting it with their own key (session key). If the ticket is valid, the guest (user) is allowed entry to the spa (resource) without revealing their original identification (username and password).

Now that the guest (user) has enjoyed the spa, they want to have dinner at the hotel’s restaurant (another service). To access the restaurant, they show their special bracelet (TGT) to the concierge (TGS) again and request a restaurant service ticket. The concierge (TGS) verifies the bracelet (TGT), issues the restaurant service ticket, and the guest (user) can dine at the restaurant without the need for re-authentication.
And to terminate our story, at the end of the day, when the guest (user) is done using various services (resources), they check out of the hotel (Kerberos realm). They return the special bracelet (TGT) to the front desk (AS) to officially end their session and authentication. Now, the guest (user) no longer has access to any services (resources) until they check in again the next time they visit the hotel (Kerberos realm).
I trust that this analogy aids in grasping the Kerberos process more effectively. However, it is essential to recognize that this is a simplified version of Kerberos. For a more comprehensive study, you can explore the following links: